Recently played with the Spring/SpringBoot/SpringCloud stack with a toy project: https://github.com/gonwan/spring-cloud-demo. Just paste README.md here, and any pull request is welcome:
Introduction
The demo project is initialized from https://github.com/carnellj/spmia-chapter10. Additions are:
- Code cleanup, bug fix, and better comments.
- Java 9+ support.
- Spring Boot 2.0 migration.
- Switch from Postgres to MySQL, and from Kafka to RabbitMQ.
- Easier local debugging by switching off service discovery and remote config file lookup.
- Kubernetes support.
- Swagger Integration.
- Spring Boot Admin Integration.
The project includes:
- [eureka-server]: Service for service discovery. Registered services are shown on its web frontend, running at 8761 port.
- [config-server]: Service for config file management. Config files can be accessed via:
http://${config-server}:8888/${appname}/${profile}. Where${appname}isspring.application.nameand${profile}is something likedev,prdordefault. - [zipkin-server]: Service to aggregate distributed tracing data, working with spring-cloud-sleuth. It runs at 9411 port. All cross service requests, message bus delivery are traced by default.
- [zuul-server]: Gateway service to route requests, running at 5555 port.
- [authentication-service]: OAuth2 enabled authentication service running at 8901. Redis is used for token cache. JWT support is also included. Spring Cloud Security 2.0 saves a lot when building this kind of services.
- [organization-service]: Application service holding organization information, running at 8085. It also acts as an OAuth2 client to
authentication-servicefor authorization. - [license-service]: Application service holding license information, running at 8080. It also acts as an OAuth2 client to
authentication-servicefor authorization. - [config]: Config files hosted to be accessed by
config-server. - [docker]: Docker compose support.
- [kubernetes]: Kubernetes support.
NOTE: The new OAuth2 support in Spring is actively being developed. All functions are merging into core Spring Security 5. As a result, current implementation is suppose to change. See:
- https://spring.io/blog/2018/01/30/next-generation-oauth-2-0-support-with-spring-security
- https://github.com/spring-projects/spring-security/wiki/OAuth-2.0-Features-Matrix
Tested Dependencies
- Java 8+
- Docker 1.13+
- Kubernetes 1.11+
Building Docker Images
In case of running out of disk space, clean up unused images and volumes with:
Running Docker Compose
Or with separate services:
Running Kubernetes
NOTE: Kubernetes does not support environment variable substitution by default.
Use Cases
Suppose you are using the kubernetes deployment.
Get OAuth2 token
curl is used here, and 31004 is the cluster-wide port of the Zuul gateway server:
Get organization info
Use the token returned from previous request.
Get license info associated with organization info
Use the token returned from previous request.
Distributed Tracing via Zipkin
Every response contains a correlation ID to help diagnose possible failures among service call. Run with curl -v to get it:
Search it in Zipkin to get all trace info, including latencies if you are interested in.
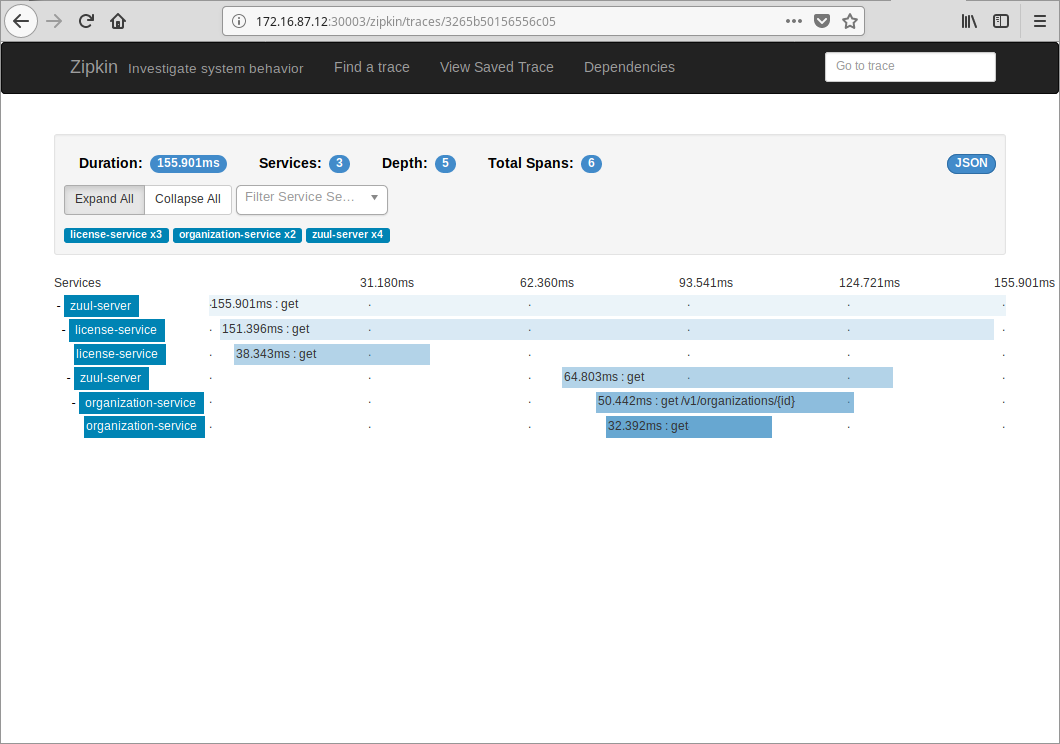
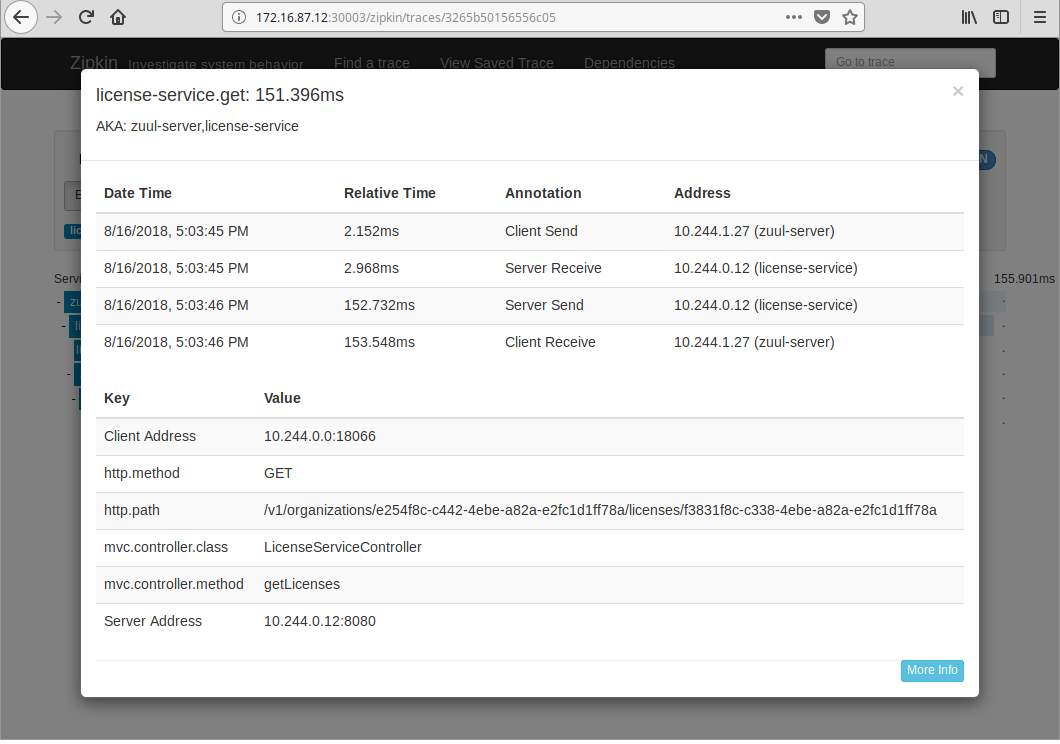
The license service caches organization info in Redis, prefixed with organizations:. So you may want to clear them to get a complete tracing of cross service invoke.
Working with OAuth2
All OAuth2 tokens are cached in Redis, prefixed with oauth2:. There is also JWT token support. Comment/Uncomment @Configuration in AuthorizationServerConfiguration and JwtAuthorizationServerConfiguration classes to switch it on/off.
Swagger Integration
The organization service and license service have Swagger integration. Access via /swagger-ui.html.
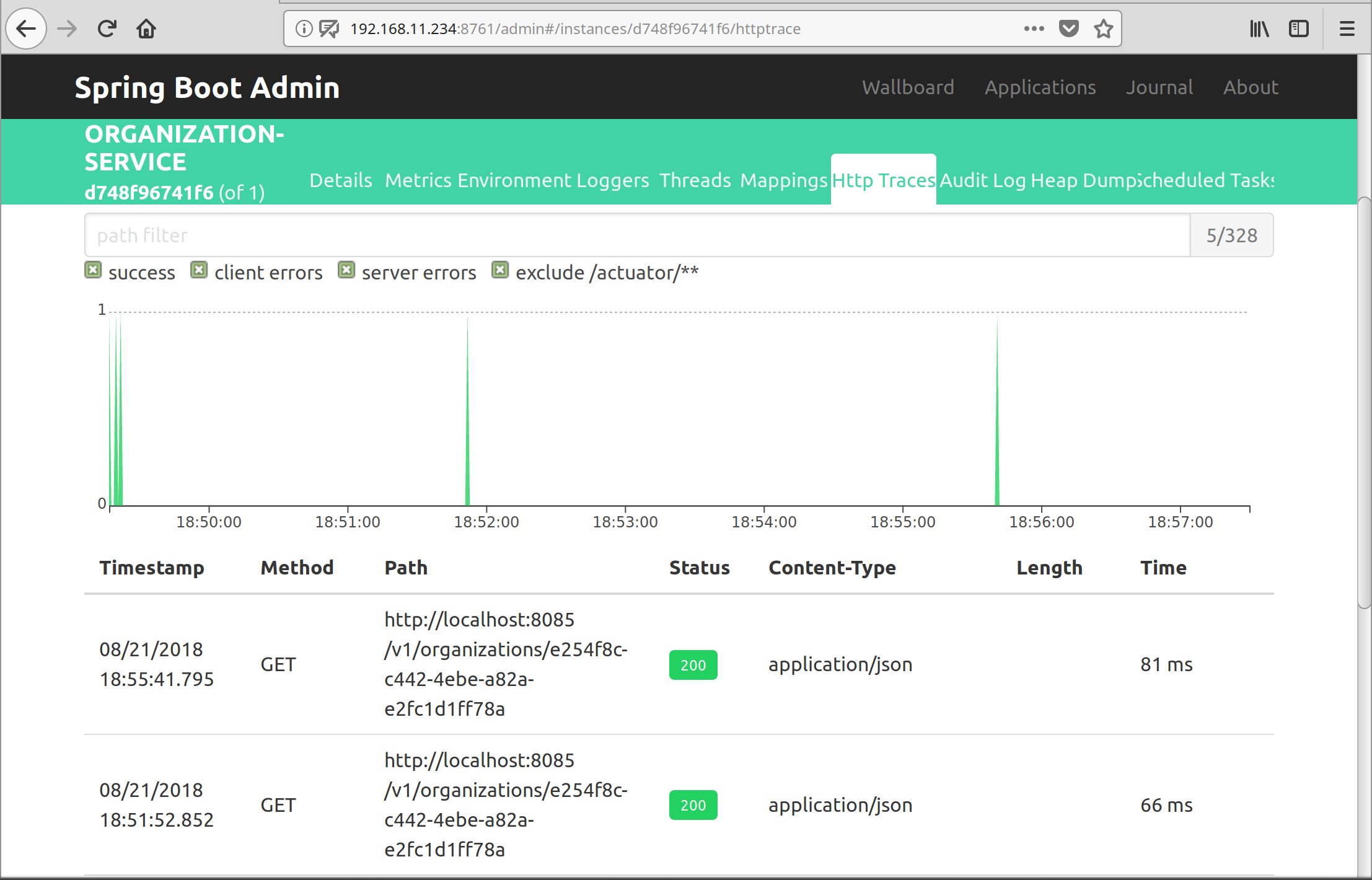
Spring Boot Admin Integration
Spring Boot Admin is integrated into the eureka server. Access via: http://${eureka-server}:8761/admin.